Side-Channel Attack Setup for Power Leakage-Based Evaluations
-
Posted by
 Red Pitaya Technical Editorial Team
, September 10, 2024
Red Pitaya Technical Editorial Team
, September 10, 2024
IoT – or the Internet-of-Things – opens up a new world that has been growing even since before the term was first coined in 1999. Not only does it make our daily lives easier, allowing us to be connected to virtually everything and everyone, but it also makes us more vulnerable with regard to information theft, with potentially grave consequences.
A side-channel attack – or SCA – is one of the ways to hunt for information through the unexpected leakage of data in any form that does not correspond to standard input or output, but nevertheless reflects what happens inside the system. In their article SCA-Pitaya: A Practical and Affordable Side-Channel Attack Setup for Power Leakage–Based Evaluations, F. Durvaux and M. Durvaux address SCAs using power leakage. This method performs Correlation Power Analysis (CPA) on the instantaneous power consumption of a device to retrieve sensitive information. These attacks have a reputation for being complicated and rather expensive, but the authors successfully set out to debunk this view in a test setup with affordable and off-the-shelf components.
The setup consisted of a data encryption system and a subsequent pickup system for data reading and decoding of the captured information. Both emitter and acquisition benches were built with low-budget mainstream components: the encryption system consisted of the 256-bit version of an Advanced Encryption Standard (AES), running on two different circuits: an 8-bit ATmega328P, embedded on an Arduino board (Uno), and a 32-bit ATSAM3X8E on an Arduino Due. Power leakage measurement was then done by means of EM radiation – emitted by the power supply pin of the chip running the algorithm – for recovery of the 256-bit key in a split second via Differential Power Analysis (DPA).
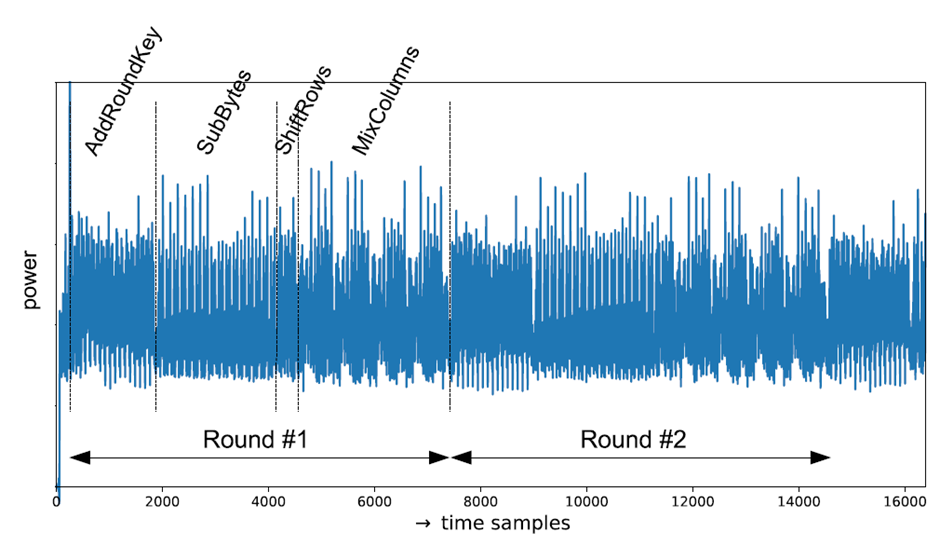
AES is a reference in symmetric encryption algorithms, available in three versions according to the different key sizes: 128, 192, or 256 bits. Encryption is done in an 8-bit architecture, implemented in C, in four layers forming a round, as can be seen in the figure below:

Figure 1: AES-256 structure overview
- AddRoundKay: a key addition layer where the round key is mixed with the input data
- SubBytes: a non-linear layer that processes 8-bit values
- ShiftRows and MixColumns: layers that contribute to the diffusion layer, designed to mix all the bits of a block.
Two different targets were built with microcontrollers with different clock frequencies on Arduino boards, as described above. The Arduino Uno included an 8-bit microcontroller with a clock frequency of 16 MHz, vs. the 32-bit chip with 84 MHz, embedded on the Arduino Due.
The RF front end – identical for both emitter setups – consisted of a 20-turn air coil probe antenna with a 6.35-mm inner diameter, a differential amplifier for common-mode noise rejection, and a homemade preamplifier. The trace acquisition was the final step of the setup hardware, using a STEMlab 125-14 board in oscilloscope configuration, sampling at its traditional 125 MS/s rate with 14-bit resolution.
After encryption, the front end picks up the instantaneous power consumption as a function of the operation in execution and the data processed, where both Poperation and Pdata are potential sources of leakages:
![]()
![]()
Differential Power Analysis is then used in the attack, exploiting the differences between traces. Key bytes are first attacked separately, before reassembly to recover the 128-bit round key, in the following sequence:
- A series of power leakage traces and their respective x-input is captured, with the s-byte identical for all traces.
- An unknown s-value (between 0 and 255) is forced to predict intermediate y- and z-values.
- For each prediction, the attacker uses a leakage model to emulate the way intermediate values are reflected in leakage traces.
- The modeled predictions are compared to observed leakage by means of a distinguisher.
The correct key is the candidate returning the highest similarity. DPA efficiency is determined by an appropriate choice of leakage model and distinguisher, depending on various parameters. Usually, a compromise between accuracy, speed and computational requirements is implemented.
After CPA attacks on the two targets (Arduino Uno and Due), obtaining exploited traces with the described side-channel attack setup, different cases were considered with varying pre-processing techniques: amplitude demodulation and projection pursuit.
Amplitude demodulation takes the absolute value of the signal samples, followed by a low-pass filter. For the Arduino boards, this could only be performed for the 8-bit architecture (with the results shown in Figure 2, below), since the 84-MHz clock frequency of the Arduino Due would require a 168-MS/s sample rate, which is higher than the 125 MS/s the STEMlab delivers. The different steps of the round operations can be clearly seen in the following figure.


Figure 2: Average demodulated power trace of the Arduino Uno
Projection pursuit is based on the observation that target bytes do not leak at a single time location. Projection weights are heuristically chosen to optimize an objective function. This optimization was performed on both targets, thanks to 5,000 training traces with known plaintexts and keys, assuming that the attacker can train on similar devices, prior to the attack. The figures below show the power spectral density and average power trace of the Arduino Due target.


Figure 3: Power spectral density of the Arduino Due power traces


Figure 4: Average power trace of the Arduino Due
For key byte recovery, the efficiency of the attacks against the first key is summarized in the success rate curves for the targets Arduino Uno and Due, shown in Figures 5 and 6 below. The impact of the pre-processing method is noticeable, especially for the apparently less complicated Arduino Uno target. This target also requires more traces compared to the Arduino Due to recover a key byte with the same level of certainty. This shows that the target complexity is not necessarily proportional to the level of difficulty of the attack. Efficiency can be further improved with more advanced leakage models and distinguishers.


Figure 5: CPA attack success rates for the Arduino Uno


Figure 6: CPA attack success rates for the Arduino Due
The final round of this experiment involves full key recovery, where the key bytes of a round are attacked independently in two phases to obtain the full AES-256 key. Each phase accounts for half of the 32-byte master key. The second round is based on the output of the first round, but the same set of attack traces is used for all key bytes. For full key recovery, the results were obtained on both target setups in times as low as 0.2-0.3 seconds, depending on the pre-processing method used.
The conclusion of this project is that the results are both impressive and worrying. The fact that many devices we use in our daily lives are actually vulnerable to attacks with affordable and easy-to-access components is a reason for deep concern. But this should not encourage the bad actors in this space, as these results can also help develop and apply countermeasures to mitigate the efficiency of an attack or enhance encryption security. No matter what, white-hat hackers will always find Red Pitaya on their side in their work to expose potential security threats.

About the Red Pitaya Team
The Red Pitaya Technical Editorial Team is a cross-functional group of technical communicators and product specialists. By synthesizing insights from our hardware developers and global research partners, we provide verified, high-value content that bridges the gap between open-source innovation and industrial-grade precision.
Our mission is to make advanced instrumentation accessible to engineers, researchers, and educators worldwide.



